Let’s Click the Link
As I previously mentioned on another platform, I encountered a Phishing website and decided to investigate. This details that investigation.
Initial Access(T1566.002) – Spearphishing Link
On 8/6/2025 at approximately 15:06:45, user John Doe received an email from <redacted> with the following contents:
In the body of the email, “View Document” is a link:
[https]://link.getmailspring.com/link/<redacted>@getmailspring[.com]/2?redirect=[https]%3A%2F%2Fprobelpremiumstore[.com].br/g63c/jAzBmD/785974/?08059scx=vlsYcH0e2Pwrjr2ldifsgRFws8DKrK&recipient=<redacted>
I am not familiar with MailSpring, but it appears they are using it for possibly for link tracking in this phishing campaign.
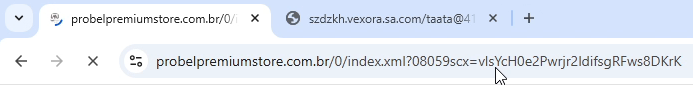
Once the link it was clicked, it redirected to the first visible redirect location (part of the original link):
[https]%3A%2F%2Fprobelpremiumstore[.com].br/g63c/jAzBmD/785974/?08059scx=vlsYcH0e2Pwrjr2ldifsgRFws8DKrK
It appeared the website wouldn’t load, then I noticed that www[.]etsy[.]com(Decoy Site(ds)1) suddenly appeared queued up:
Because the site continued to hang, I decided to reload the page. This time I was immediately brought to ds1,
So, I reloaded the page again…hangs….and again.
This time I see 2 documents:
index.xml and index.xslt:
To get index.xslt, I planned on using the location of the GET request:
But, just as I copied the URL, I was redirected again:
It stopped with a breakpoint(?):
Whether I continue through, or step-over, I am redirected to the ds. Unfortunately, because the page is blank, there were no Elements to inspect.
At this point, I spent quite a while trying to figure out how to reverse what is going on here. If you want to know how long…ask me.
Eventually, I went back to the index.xlst file that I pulled from earlier:
I renamed(unnecessary) the file for the syntax highlighting in Notepad++:
Here is where the last redirect before the ds is located. It appears the redirect flow is as follows:
[https]://link.getmailspring.com/link/<redacted>@getmailspring[.com]/2?redirect=[https]%3A%2F%2Fprobelpremiumstore[.com].br/g63c/jAzBmD/785974/?08059scx=vlsYcH0e2Pwrjr2ldifsgRFws8DKrK&recipient=<redacted>
To
[https]%3A%2F%2Fprobelpremiumstore[.com].br/g63c/jAzBmD/785974/?08059scx=vlsYcH0e2Pwrjr2ldifsgRFws8DKrK
To
Which sends a GET request for
Which is an xml that contains our last redirect before ds
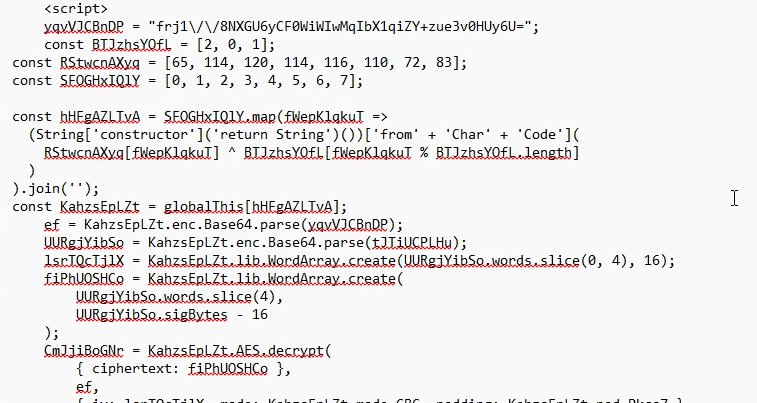
This site becomes the target. Looking at the text, It was clearly all heavily obfuscated and encrypted Javascript:
After running the page through AI, it was determined that we needed to find the value of mSULBD1sMF .
While most of the variables seemed benign, mSULBD1sMF appeared to be quite interesting:
It becomes quite clear that the functions of this script are likely the following:
· generate a fake cloudflare turnstile.
· Store formdata in r7
· Send a GET request to
· If the page responds with a 0
· Send a POST request containing the data from r7 to the current site appending
to the url. I then began trying to understand where the next page should be:
At this point I felt like I was playing a CTF, being railroaded by the actor. Still wanting to explore, I tried something else. This is when I determined that I could not continue with this phishing site if I continue to get detected and redirected so I decided to allow the site to load. Here is the madness that ensued:
I had to click the buttons
We made it to the Phishing page. Since we already reviewed the mechanics of the page, we know how it works. Lets look a bit deeper.
Remember, at this stage:
· all the relative hotkeys are disabled(to prevent analysis)
· if the debugger is detected, the page will redirect to a ds.(again, to prevent analysis)
But we must continue to investigate. I decided to test the debugger checker by manually opening Dev Tools:
Of course.
But there is a silver lining:
I had to again remind myself that this was not a CTF. The actor insisted on keeping me motivated.
With my new found motivation, my next goal was to get a copy of this HTML code.
The more I looked through the code, the more it became clear that this was a phishing kit:
I then decided to try saving the page:
I will attach some excerpts with a bit of commentary:
This kit includes instructions for getting debugging help
Includes provisions for stealing 2fa codes
More Phishing kit snippets:
I think that I could probably look a bit deeper, but that is all I have for now. Thank you for your time. Until we meet again.